It is becoming increasingly important to be aware of who might be monitoring your online activity. Whether it's your employer, a family member, or a malicious hacker, there are many threats to your privacy. While not all third-party spying methods can be spotted, there are several ways to get an idea of who is monitoring your activity. For example, you can check your taskbar for suspicious programs or use the Command window to generate a list of all outgoing data transmissions. You can also compare website certificate fingerprints to verify the validity of a website's certificate.
| Characteristics | Values |
|---|---|
| Check the taskbar | Most Internet-monitoring programs have an icon that appears on the Windows taskbar |
| Windows Firewall | Click on "Exceptions" to view all programs that have access to your computer |
| Windows Task Manager | Press "Ctl," "Alt" and "Delete" simultaneously to view all active processes on your computer |
| Internet Explorer | If the "Proxy Server" checkbox is ticked, it means that a third party can log your activity |
| Command window | Type "netstat" to generate a list of all outgoing data transmissions |
| Task Manager | View the "User Name" of all processes running on your computer. Processes that do not include your username may be an indication of malicious software |
| SSL Inspection Platforms | Corporations can use these to strip encryption from traffic |
| SSL Proxy | A computer that intercepts your computer’s request for an encrypted web page, makes the request for you, decrypts the traffic, inspects it, then re-encrypts it and sends it back to you |
What You'll Learn

Check your taskbar for suspicious programs
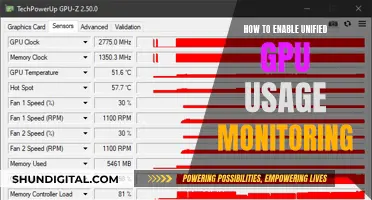
If you're concerned that your internet activity is being monitored, one of the first things you can do is check your taskbar for suspicious programs.
On a Windows device, the taskbar is located at the bottom right-hand corner of your screen. Here, you can examine the programs that are running and identify any that seem out of place. Most internet-monitoring programs will have an icon that appears in this taskbar.
If you're unsure about a particular program, you can right-click on the taskbar and select 'Task Manager' to open the Windows Task Manager. This will allow you to view all the active processes on your computer and identify any that are consuming a large amount of system resources. Be cautious of processes running under a different user name or with a description that deviates from the norm, as these are often suspicious.
Once you've identified a potentially suspicious process, you can right-click on it and select 'Search online' to learn more about it. This will help you verify whether the process is legitimate or potentially malicious. If you determine that it is indeed malicious, you can end and remove it from your device by following the steps outlined in the Windows Task Manager.
It's important to note that not all third-party spying methods can be easily spotted, and some spyware is designed to remain hidden. However, by regularly checking your taskbar and actively managing your computer's processes, you can enhance your chances of detecting and removing any suspicious programs.
Connecting Monitors to Home Security Cameras: A Step-by-Step Guide
You may want to see also

Check for open ports in your firewall
To check for open ports in your firewall, you can use various tools and methods depending on your operating system. Here are some detailed instructions for checking open ports on Windows and Mac devices:
Windows
- Using Telnet: First, enable Telnet by going to the Windows Features settings and checking the box next to Telnet Client. Open a command prompt by typing "cmd" into the Windows search bar and pressing Enter. Then, type "ipconfig" and press Enter to display your network information. Write down your router's IP address, which will be next to "Default Gateway". Next, type "telnet" and press Enter to open the Microsoft Telnet prompt. Finally, type "open [IP address] [port number]" to check if a specific port is open. For example, type "open 10.0.0.1 25" to check if port 25 is open on your router. Press Enter, and if Telnet connects, the port is open.
- Using Windows Firewall Settings: Open the Windows Start menu and select "Control Panel". Click "Windows Firewall" and then click the "Exceptions" tab. Here, you can view all the programs that have been granted access to your computer and have opened ports in your firewall. If you see any suspicious programs, you can search online to find out more about them.
- Using Windows Task Manager: Press Ctrl + Alt + Delete simultaneously to launch the Windows Task Manager. Click the "Processes" tab to view all active processes on your computer. If you see any processes running under a different username, investigate further to check for potential monitoring software.
- Using Internet Explorer: Open Internet Explorer and click on "Tools", then "Internet Options". Select "Connections" and click on "LAN Settings". If the checkbox under "Proxy Server" is checked and you see a local IP address in the box, it means that your web activity can be logged by a third party.
Mac
- Using Terminal: Open a Terminal window by opening Spotlight (magnifying glass in the top-right corner) and typing "terminal". Type "netstat -nr | grep default" and press Enter to find your router's IP address. Next, type "nc -vz [your router's IP address] [port number]" to check if a specific port is open. For example, type "nc -vz 10.0.0.1 25" to check if port 25 is open. Press Enter, and if you see a message that the connection succeeded, the port is open.
- Using Mac Firewall Settings: Go to System Preferences and click on "Security & Privacy". Click on the "Firewall" tab, and if you see "Firewall: On", your firewall is active. Click on "Firewall Options" to view the list of apps and services that are allowed or disallowed from incoming connections. If an app or service has a green dot next to it, its port is open.
In addition to these methods, there are also online tools available, such as open port checker tools, that can help you scan your network for open ports. These tools can be useful for detecting if your port forwarding is set up correctly or if certain ports are being blocked by a firewall or ISP.
Connecting a Chromebook to a Monitor: A Simple Guide
You may want to see also

Check for unknown processes in Task Manager
If you're concerned that your internet traffic is being monitored, one way to check is by examining your computer's Task Manager for any unknown or suspicious processes. Here's a detailed guide on how to do this:
- Opening Task Manager: On Windows, simultaneously press the "Ctrl" + "Shift" + "Esc" keys on your keyboard to open the Task Manager. Alternatively, you can right-click on the taskbar and select "Task Manager" or "Start Task Manager" from the menu. For macOS, press "Command" + "Spacebar" to open Spotlight search, then search for and select "Activity Monitor".
- Locating Unknown Processes: Once the Task Manager is open, navigate to the Processes tab. Here, you will see a list of all the running processes on your computer. Look for any processes that seem unfamiliar or suspicious. Pay attention to processes that are consuming a significant amount of system resources, such as CPU or memory.
- Investigating Suspicious Processes: If you find a process that you don't recognize or seems unusual, right-click on it and select "Search online" or "Open file location". This will allow you to research the process and verify whether it is legitimate or potentially malicious. You can also document the process name and investigate its use by searching for it online.
- Ending and Removing Suspicious Processes: If, after investigating, you determine that a process is malicious or unwanted, you can end and remove it. Right-click on the suspicious process and choose "End Task" or "End Process" to stop it from running. You can then delete any associated files and uninstall any related applications.
It's important to note that some monitoring software may be designed to run stealthily and may not appear in the Task Manager. Additionally, your IT administrator may have configured your system to hide certain monitoring programs. Therefore, it's crucial to combine this method with other techniques, such as checking for unknown programs, monitoring your webcam activity, and reviewing active internet connections.
Brighten Your View: Adjusting LCD Monitor Brightness
You may want to see also

Check LAN settings for proxy servers
If you suspect that your internet traffic is being monitored, one thing you can do is check your LAN settings for proxy servers. Here's a detailed guide on how to do that:
Check Proxy Settings in Windows
Most browsers will use the proxy settings that are configured on your computer. Each browser has its own settings page to adjust proxy settings, but they usually just link to the settings dialog in Windows itself.
Windows 10/11 Settings App
To check proxy settings in Windows 10 or 11, follow these steps:
- Click on the Start button and then click on the gear icon (Settings) in the bottom-left corner.
- In the Settings menu, click on "Network & Internet".
- In the left pane, scroll down and click on "Proxy" at the bottom.
- Here, you'll see two configurations: Automatic or Manual proxy setup. In most cases, everything should be set to Off. If anything is turned on, it means your web traffic could be going through a proxy server.
Windows Control Panel
You can also check proxy settings through the Control Panel, which works for older versions of Windows:
- Click on Start and open the Control Panel.
- In the Control Panel, locate and click on "Internet Options".
- In the Internet Options dialog, go to the "Connections" tab and then click on "LAN settings" at the bottom.
- Here, you'll see the same proxy settings as in the Settings app. Anything configured here will reflect in the Settings app and vice versa.
Check Proxy Settings in Mac OS X
If you're using a Mac with OS X, follow these steps:
- Open System Preferences and click on "Network".
- On the left-hand side, select the connected or active network connection. You can set different proxy settings for each type of network connection.
- Click on the "Advanced" button and then click on the "Proxies" tab. Here, you'll see a list of different proxy protocols that can be configured.
- For example, if you click on "Web Proxy (HTTP)", you can enter the proxy server IP address, port number, username, and password.
Check Proxy Settings in Linux
The process for checking proxy settings in Linux depends on the distribution you're using. For example:
- Ubuntu: Open System Settings, scroll down to Hardware, click on "Network", and then "Network Proxy".
- Linux Mint Cinnamon: Click on System Settings, scroll down to Hardware, click on "Networking", and then "Network Proxy".
In most Linux distributions, you'll have the option to choose between Automatic or Manual proxy setup.
A proxy server is an intermediary between your device and the internet. It's usually configured in corporate environments to filter and monitor web traffic to and from employee computers. While proxy servers have legitimate uses, they can also be used to monitor internet activity without your knowledge.
Monitoring Kids' Social Media: Parenting in the Digital Age
You may want to see also

Check for SSL certificate warnings
Checking for SSL certificate warnings is an important step in determining if your internet traffic is being monitored. SSL certificates are essential for securing online communications and protecting sensitive information. Here are some detailed instructions on how to check for SSL certificate warnings:
Check the Website URL:
The first step is to examine the URL of the website you're visiting. A secure website will typically start with "https://" instead of just "http://". The "s" in "https" stands for "secure" and indicates that the website is using SSL (Secure Socket Layer) encryption. This is often the quickest way to identify if a website has an SSL certificate.
Look for the Padlock Icon:
Modern web browsers also provide visual cues to help you determine if a website is secure. Look for a padlock icon in the address bar next to the URL. Clicking on this padlock will usually display detailed information about the website's security, including the SSL certificate. This is a simple way to verify the security of the site you're visiting.
Check Certificate Details:
When you click on the padlock icon, you'll be able to see various details about the SSL certificate. This includes the certificate's expiration date, the issuing authority, and the level of validation. Ensure the certificate is still valid and issued by a trusted source. If the certificate is expired or issued by an untrusted entity, it may be a warning sign.
Verify Correct Hostname:
It's important to ensure that the hostname included in the SSL certificate matches the website's URL. Mismatched hostnames can indicate a potential security issue or an attempt to impersonate a legitimate website. Always check that the hostname in the certificate corresponds to the site you're visiting.
Be Wary of Untrusted Warnings:
If a website's SSL certificate is not trusted by your browser, you may encounter warning messages or errors. These warnings could indicate that the certificate is not issued by a recognised authority or that there are issues with intermediate certificates. Heed these warnings and be cautious about proceeding, especially if you're sharing sensitive information.
Use SSL Checker Tools:
There are online tools available, such as SSL Checker, that can help you diagnose problems with SSL certificates. These tools allow you to verify the SSL certificate on a web server and ensure it is correctly installed, valid, and trusted. They can also check for issues like incorrect intermediate certificates and old hash functions. Using such tools can provide you with additional peace of mind.
By following these steps and staying vigilant, you can help protect yourself from potential security threats and ensure your online communications are secure. Remember to look out for SSL certificate warnings and take appropriate action to safeguard your personal information.
Business Tech: Monitoring Resource Usage for Efficiency
You may want to see also
Frequently asked questions
If you have access to your company's network settings, you can check the firewall settings and exceptions to see if any unknown programs have been granted access to your computer. You can also check the running processes on your computer and investigate any that seem suspicious. However, it's important to note that not all third-party spying methods can be spotted.
If you see a lock symbol in the address bar of your web browser, it indicates that your connection to the website is secure, and your traffic is encrypted. If you see a broken lock symbol, it means that your connection is not secure, and someone may be trying to spy on your web browsing.
Employers, family members, or hackers may use stealth apps such as keystroke loggers and traffic monitors to track online activity. They can also use software installed on your computer or filter internet traffic through a central point on their network.
Yes, if your personal devices are connected to a company network, your employer may be able to see your network activities, including websites visited. It is recommended to keep personal devices off corporate networks.
To protect your privacy, avoid using public or shared computers for sensitive tasks such as accessing personal accounts. Use your own devices, and ensure that your connections to websites are secure, as indicated by the lock symbol in the address bar.