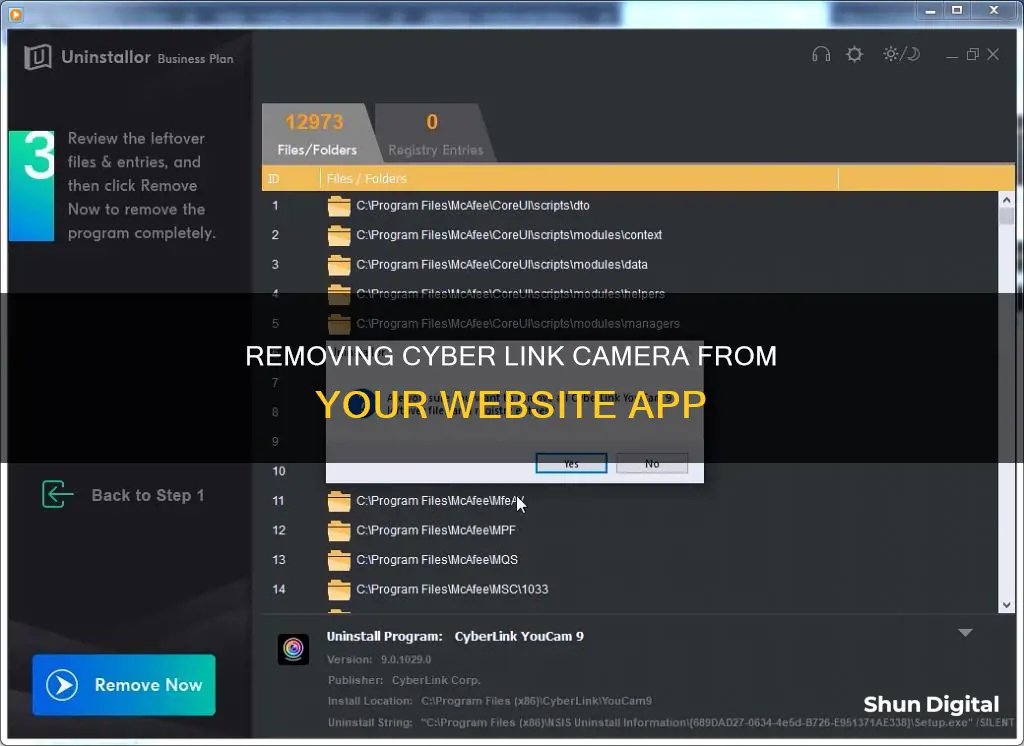
CyberLink YouCam is a popular webcam software that enhances your video chats and recordings with fun effects, filters, and enhancements. It is compatible with various video chat applications such as Skype, Zoom, and Facebook Messenger. While it offers exciting features, some users may want to remove it due to compatibility issues, performance, or privacy concerns. Uninstalling CyberLink YouCam can be done through the Control Panel on Windows or by using third-party uninstaller tools like Revo Uninstaller Pro. This paragraph introduces the topic of how to remove CyberLink's camera functionality from a website or application, which will be further explored in the following paragraphs.
| Characteristics | Values |
|---|---|
| Operating Systems | Windows, macOS |
| Uninstallation Process | Via Control Panel, Third-Party Uninstaller, Apps and Features/Programs and Features, CyberLink's Uninstaller.exe, or Run Command |
| Reasons for Uninstallation | Incompatibility with other applications, frequent crashes or hangs, lower quality than expected, reinstallation required, security concerns, freeing up storage space, privacy concerns |
What You'll Learn

Uninstall CyberLink YouCam using Control Panel
Uninstalling CyberLink YouCam can be done in a few simple steps using the Control Panel on Windows.
First, open the Control Panel by clicking the "Start" button on your Windows screen and selecting "Control Panel" from the menu. You can also try using the Windows key + X shortcut and selecting Control Panel from the menu that appears.
Once the Control Panel is open, look for the "Programs" section. Here, you will find options such as "Uninstall a Program" or "Programs and Features," depending on your Windows version. Click on the appropriate option.
Next, locate "CyberLink YouCam" in the list of installed programs. Right-click on it and select "Uninstall" or "Remove." Follow any additional on-screen instructions to complete the uninstallation process.
In some cases, you may need to confirm the uninstallation by clicking "Yes" when asked if you want to completely remove the product. After the uninstallation is complete, it is recommended to reboot your computer.
Please note that uninstalling CyberLink software will permanently remove the application from your computer, and you will no longer be able to open projects or works created with CyberLink software on your machine.
Pentax Camera Identification: A Guide to Knowing Your Model
You may want to see also

Use a third-party uninstaller
If you're looking for a quick and easy solution to remove CyberLink YouCam from your computer, you may want to consider using a third-party uninstaller like Bloatware Uninstaller. This option can be especially helpful if you're facing challenges with the standard uninstallation process or if you want to ensure a thorough removal of all associated files.
Bloatware Uninstaller is a user-friendly tool that comes with a collection of toolkits designed to safely and completely uninstall CyberLink YouCam. It achieves this by removing associated registry keys and program files, ensuring that no traces of the software are left behind. Here's a step-by-step guide on how to use Bloatware Uninstaller to remove CyberLink YouCam:
Step 1: Launch Bloatware Uninstaller
Begin by launching the Bloatware Uninstaller application on your computer. This software will guide you through the uninstallation process, making it more straightforward and efficient.
Step 2: Select CyberLink YouCam for Removal
Once the uninstaller is open, you'll see a list of installed programs. Find and select CyberLink YouCam from this list, indicating that this is the target program you want to remove. Then, hit the "Run Analysis" button to initiate the process.
Step 3: Initiate the Uninstallation
After analyzing the program, the uninstaller will present you with an "Complete Uninstall" button. Press this button to continue with the uninstallation process. Follow any additional on-screen instructions provided by the uninstaller to proceed.
Step 4: Scan and Delete Leftover Files
As the uninstallation process nears completion, you'll see the "Scan Leftovers" button light up. Click on it, and then select the "Delete Leftovers" option to ensure that all traces of CyberLink YouCam are removed from your computer. This step is crucial to ensure a thorough uninstallation.
Additional Considerations:
It's important to note that CyberLink YouCam may have an associated program called CyberLink PerfectCam. If this is the case, you'll need to repeat the same steps to uninstall CyberLink PerfectCam after removing CyberLink YouCam. Additionally, always ensure that you uninstall the target program first to avoid any issues with leftover files.
Using a third-party uninstaller like Bloatware Uninstaller can be a convenient and efficient way to remove CyberLink YouCam from your computer. It simplifies the process, ensuring a complete removal without causing any damage to critical system files. Remember to follow the recommended steps and precautions for a smooth uninstallation experience.
Removing the Samsung S4 Camera: A Step-by-Step Guide
You may want to see also

Uninstall using the program's built-in uninstaller
Uninstalling CyberLink software will permanently remove the application from your computer. Before you uninstall, it is important to understand that any projects or works created with CyberLink software will no longer be accessible on your computer. Additionally, if you are uninstalling the CyberLink trial version, this will not reset your computer or extend its trial period.
To uninstall using the program's built-in uninstaller, follow these steps:
Method 1: Using the Control Panel
- Go to the Start menu and click "Control Panel".
- Click "Uninstall a Program", which is located in the "Programs" section.
- Select the CyberLink product you want to uninstall by clicking on it, then click "Uninstall/Change".
- When asked if you want to completely remove the product, click "Yes".
- When prompted to reboot your computer, click "Yes" again.
Method 2: Using the Start Menu
- Right-click on the Start menu.
- Select "Control Panel" from the dropdown menu.
- Click on "Programs and Features".
- Select the CyberLink product you wish to uninstall and click "Uninstall/Change".
- Confirm that you want to completely remove the product by clicking "Yes".
- When prompted to reboot, click "Yes" to restart your computer.
Please note that you should not attempt to manually uninstall or remove CyberLink software by dragging folders to the Recycle Bin, as this can cause irreversible problems if you intend to reinstall the product in the future.
Troubleshooting Blue TV Screen Issues on Camera
You may want to see also

Uninstall using the Run command
To uninstall CyberLink using the Run command, follow these steps:
- Press the Windows key + R on your keyboard to open the Run dialog box.
- Copy and paste the following uninstallation string into the Run command window: "C:\Program Files (x86)\NSIS Uninstall Information\{EE9EC028-49D2-4349-B0A3-9B2E752A4958}\Setup.exe" _?=C:\Program Files (x86)\NSIS Uninstall Information\{EE9EC028-49D2-4349-B0A3-9B2E752A4958}
- Click OK.
- Follow the on-screen instructions to complete the uninstallation process.
Using the Run command is an effective way to uninstall CyberLink software, but it's important to note that this method may not work for all versions of the software. The uninstallation string provided is specific to CyberLink PowerDirector, so if you are using a different version, the string may be different.
Additionally, before proceeding with the uninstallation, it is recommended to understand the implications of removing CyberLink from your system. Any projects or works created with CyberLink software will no longer be accessible on your computer. Furthermore, uninstalling a trial version of CyberLink will not reset your computer's trial period. It is also crucial to refrain from manually deleting CyberLink software by dragging folders to the Recycle Bin, as this can cause irreversible issues when attempting to reinstall the product in the future.
Uninstalling Camera App: A Guide for Android Users
You may want to see also

Potential security concerns
Security cameras are increasingly internet-connected, driven by the desire for remote access, control, integration, and reduced cloud storage costs. However, this connectivity also exposes them to potential cyber-attacks, creating a dangerous door for hackers to access sensitive information and systems. Here are some potential security concerns related to web-connected cameras:
Vulnerabilities in Mobile Apps: Security flaws in mobile applications that control security cameras can allow hackers to gain remote access to images, videos, and settings. For example, flaws in the Kasa mobile app, used for TP-Link's range of Kasa home security cameras, could be exploited to access sensitive information.
Weak Passwords: Many cameras share the same default password, which is often weak and easily guessable. This is a significant security risk, as it allows hackers to gain unauthorized access to the camera systems.
Insecure Connections: Some camera systems use unencrypted connections, which can lead to password vulnerability and potential privacy and eavesdropping breaches. It is crucial to use encrypted connections, such as SSL or equivalent, to protect sensitive data.
Operating System Vulnerabilities: All operating systems have vulnerabilities, and it is important to keep them up-to-date with security patches. Windows-based systems are known to have many vulnerabilities, and Linux-based systems are not exempt, with exploits like Shellshock and Ghost making millions of systems vulnerable.
Network Topology: Connecting security camera systems to the main network can create a doorway for hackers to access other systems. It is recommended to place the camera system on a physically separate network or use a VLAN to minimize the risk.
Botnets: Botnets are a common threat to commercial cameras, where malware infects multiple devices and uses them for criminal activities such as cryptomining, DDoS attacks, and credential stuffing. This can lead to high energy bills and put physical safety at risk.
Spying and Data Theft: Hackers can use compromised cameras to spy on companies through video and audio feeds, monitoring sensitive areas like boardrooms and executive conference rooms. Additionally, cameras can be a blind spot for IT teams, making it difficult to detect data exfiltration, as they don't typically monitor camera network traffic.
Pivot Attacks: Hackers can use compromised cameras as a base to launch further attacks, exploiting their access to the local IT environment and the cloud. This enables them to move deeper into the company network while avoiding detection.
Firmware and Software Updates: Outdated firmware and software can introduce security vulnerabilities. It is essential to keep camera firmware and the software that manages them up-to-date to prevent potential exploits.
Uncover Camera Details: Unraveling Image Metadata Secrets
You may want to see also







