Hacking into someone's computer camera is an invasion of privacy and is illegal. This answer is for educational purposes only and should not be used for malicious purposes.
Hacking into a computer camera is possible, and there are several ways to do it. One common method is to gain access to the target's computer by tricking them into clicking on a malicious link or file. This allows the hacker to install malware, such as a remote-control Trojan, that gives them access to the camera and other personal files. Another method is to use default passwords that many people don't change, allowing easy access to the camera. More advanced techniques involve using tools like Meterpreter to exploit vulnerabilities in the target's system and gain control of their webcam.
To protect yourself from webcam hacking, it is important to keep your operating system and applications updated, use reliable antivirus software, and cover your webcam when not in use.
| Characteristics | Values |
|---|---|
| Purpose | Blackmail, steal photos and videos, or to spy |
| Hacking definition | To get something or to break into someone’s personal data without their consent |
| Difficulty | Not easy, but possible |
| IP address | Dynamic, changes daily |
| Tools | Telnet, FTP, IMAP, HTTP authentication, POP3, Net-bios, LDAPNNTP, PCNFS, ICQ |
| Port scanner | Advanced |
| Anti-hacking components | Trobing Webcam Cover, anti-hacking software |
| Malware | Remote-control malware |
| Prevention | Tape over camera, use anti-virus software, avoid phishing traps, use a VPN on public Wi-Fi |
What You'll Learn

Use a website that lists hacked CCTV cameras
Using a website that lists hacked CCTV cameras is the easiest method for viewing unsecured cameras. These websites are created by hackers who gain access to IP CCTV cameras or DVRs (Digital Video Recorders) and make the footage available for others to view. Websites such as Insecam and Opentopia list unsecured cameras from all over the world and allow anyone to watch the live streams. Insecam, for example, has over 100,000 cameras listed, and also provides information such as the camera manufacturer, default login and password, time zone, city, and a pinpointed location on Google Maps.
The process of hacking into these cameras usually involves trying the default username and password, as many people do not change these when they install a new camera. Websites and hackers take advantage of this by randomly inputting default usernames and passwords until they gain access to the camera.
To protect your cameras from being hacked, it is important to change the default username and password, and to regularly update your firmware to patch security vulnerabilities. It is also recommended to buy cameras from reputable brands, as they offer continuous technical support and release updates for their firmware.
After Effects Camera Modes: Choosing the Right One
You may want to see also

Hack CCTV cameras using default passwords
Overview
This guide will take you through the process of hacking into CCTV cameras by exploiting default passwords. It's important to note that this is for educational purposes only and you should not attempt to hack into cameras that don't belong to you. By understanding how these hacks work, you can better protect your own devices.
Tools Required
- Angry IP Scanner: A powerful GUI port scanner available for Windows, macOS, and Linux.
- Hydra: A brute force tool that can be used to crack passwords.
Step 1: Download and Install Angry IP Scanner
Visit the Angry IP Scanner website and download the appropriate version for your operating system. Install the software by following the installation instructions.
Step 2: Configure Angry IP Scanner
Open Angry IP Scanner and go to "Tools > Preferences > Ports". Add the following ports: 80, 8080, and 23. These are commonly used ports for CCTV cameras and routers.
Step 3: Choose IP Address Range
To hack into CCTV cameras, you need to find their IP addresses. CCTV cameras are typically connected to broadband internet connections. Find your public IP address by searching "My IP" on a search engine. The IP range can then be determined by modifying the last segment of your IP address.
Step 4: Start IP Range Scanning
Enter the IP range in the Angry IP Scanner and start the scan. This process may take some time, depending on the range you specified.
Step 5: Locate CCTV Cameras
Once the scan is complete, you will see a list of devices and their details. Look for entries that indicate CCTV cameras, such as "DVRDVS-Webs" or "Hikvision-Webs". Copy the IP address of the CCTV camera you want to target.
Step 6: Attempt Default Passwords
Open a web browser and enter the IP address of the CCTV camera. You will be presented with a login screen. The default username and password for many CCTV cameras are "admin". Try different combinations, such as "admin/admin" or "admin/12345". You can also search online for default username and password lists for specific camera models.
Step 7: Crack Password with Hydra (Optional)
If the default passwords don't work, you can attempt to crack the password using Hydra. Hydra is a brute force tool that tries different password combinations until it finds the correct one. You will need a wordlist containing potential passwords to use with Hydra.
Warning
Hacking into CCTV cameras without authorization is illegal and unethical. This guide is for educational purposes only to raise awareness of the importance of securing your devices with strong passwords. Always respect the privacy of others and use your knowledge responsibly.
Burst Mode: Capturing Fast-Paced Action with Your Camera
You may want to see also

Hack CCTV cameras using Shodan
Shodan is a search engine that allows users to find devices connected to the internet, including IP cameras, routers, servers, traffic lights, SCADA systems, and medical equipment. It was originally created by John Matherly to help companies find devices connected to the internet using their software.
Shodan has indexed information on more than 500 million devices monthly, and it is often used to search for vulnerable devices that are connected to the internet when an exploit is discovered. Many of the devices indexed on Shodan do not require credentials to access them. This leaves them exposed to anyone who comes across them on Shodan.
- Log in to Shodan: Go to shodanhq.com in a web browser and log in. Shodan restricts some capabilities to logged-in users. For instance, you can only view one page of search results without logging in, and two pages of search results with a free account.
- Set up Shodan via the command line (optional): You don't need to open a web browser to use Shodan if you know your API Key. To install Shodan, you'll need a working Python installation. Then, you can use the command line to install the Shodan library.
- Search for accessible webcams: You can usually find webcams on Shodan by using the name of the webcam's manufacturer or webcam server. Shodan indexes information in the banner, so if the manufacturer puts its name in the banner, you can search by it. For example, "webcamxp" pulls up links to thousands of web-enabled security cameras around the world.
- Try default usernames and passwords: Many of the webcams Shodan shows will require authentication. Try the default username and password for the security camera hardware or software. Common default usernames and passwords include admin/123456, root/pass, and admin/admin.
- Search for webcams by geography: You can be more specific in your search by trying to find webcams in a particular geographical location. For example, if you wanted to find WebcamXP cameras in Australia, you could search "webcamxp country:AU".
- Narrow your search to a city: You can further narrow your search by specifying an individual city. For example, to find WebcamXP cameras in Sydney, Australia, you could search "webcamxp city:sydney".
- Find webcams by longitude and latitude: Shodan allows you to be very specific in your search by enabling you to search for web-enabled devices by their longitude and latitude. For example, to find WebcamXP cameras in Melbourne, Australia, you could search "webcamxp geo:-37.81,144.96".
Remember that accessing CCTV cameras without authorization is illegal in many jurisdictions and may result in legal consequences. This information is provided for educational purposes only.
Charging Camera Pens: A Quick Guide to Powering Up Discreetly
You may want to see also

Hack CCTV cameras using exploit tools
Exploits are a type of attack that takes advantage of vulnerabilities in a system, such as a security flaw or a bug. In the context of CCTV cameras, an exploit tool can be used to gain unauthorized access to the camera's functions and data. Here are the steps to hack CCTV cameras using exploit tools:
Step 1: Identify the CCTV Camera Model and Firmware Version
To use an exploit tool effectively, you need to know the specific model and firmware version of the CCTV camera you are targeting. This information can often be found in the camera's manual or by searching online.
Step 2: Search for Exploits
Once you have identified the CCTV camera model and firmware version, you can search for known exploits associated with that particular model and version. This can be done by searching online, usually on websites or forums dedicated to security research and hacking.
Step 3: Find or Develop an Exploit Tool
After identifying a relevant exploit, you need to find or develop a tool that can take advantage of the vulnerability. In some cases, exploit tools may be readily available for download, while in other cases, you may need to develop your own tool or modify an existing one.
Step 4: Gather Necessary Information
Before using the exploit tool, gather all the necessary information about the target CCTV camera, such as its IP address, port number, and any relevant credentials. This information will be used as input for the exploit tool.
Step 5: Run the Exploit Tool
With the exploit tool in hand and the necessary information gathered, you are now ready to run the exploit. Follow the specific instructions provided with the exploit tool, as each tool may have unique requirements and usage guidelines.
Example: Hikvision IP Camera Exploit
One well-known example of a CCTV camera exploit is the Hikvision IP camera exploit, which was discovered in March 2017. This exploit affects certain models of Hikvision IP cameras that are using old firmware versions. The exploit allows direct access to device information, including the model, serial number, firmware version, and user credentials.
To use this exploit, you would need to download the Hikvision Backdoor exploit tool and run it on a computer or laptop. You would then input the target camera's IP address and port number, click "get user list," select the user whose password you want to change, and then type a new password. After confirming the new password, you would be able to access the camera's functions and data.
It is important to note that exploiting CCTV cameras without authorization is illegal and unethical. The information provided here is for educational purposes only, and you should not attempt to hack into any CCTV camera without explicit permission from the owner.
Focus Bracketing: Which Cameras Offer This Feature?
You may want to see also

Hack CCTV cameras using a simple command
This guide will take you through the process of hacking into CCTV cameras using a simple command. It is important to note that this information is being shared to make you aware of the possibility of such an attack and to help you protect yourself against it.
Understanding the Basics
Before we delve into the steps, let's clarify some basic concepts.
- CMD (Command Prompt): This is a Windows command-line interpreter used to execute commands to perform various tasks on your computer.
- IP Address: This is a unique address that identifies a device on the internet. Think of it like a home address for your computer or any other device connected to the web.
- Port: In the context of networking, a port serves as a gateway for incoming and outgoing data. Different applications or services often use specific ports.
Step-by-Step Guide to Hacking CCTV Cameras
Now, let's get into the specifics of how one might hack into CCTV cameras using a simple command.
Finding the IP Address Range:
- CCTV cameras are typically connected to a broadband internet connection. To hack into them, you need to find the correct IP address range.
- Start by finding your public IP address. You can do this by simply searching for "My IP" on search engines like Google or Bing. For example, if your public IP address is "77.247.181.165," the IP range could be "77.247.181.1" to "77.247.181.255."
Using Angry IP Scanner:
- Download and install Angry IP Scanner, a powerful GUI-based port scanner available for major operating systems.
- Open Angry IP Scanner and go to "Tools > Preferences > Ports." Add the ports "80," "8080," and "23" in the Port Selection tab. This will scan these specific ports.
- Go to "Tools > Fetchers > Add (<<) web detect." This will allow you to see brief details about the devices connected to the internet, such as the CCTV camera model name and router information.
Scanning the IP Range:
- In Angry IP Scanner, add the IP range you want to scan in the "IP Range" tab, and then click "Start."
- After the scan is finished, you will find interesting information in the "Web Detect" tab. Look for entries that indicate CCTV cameras, such as "uc-httpd 1.0.0" or "DVRDVS-Webs."
Default Username and Password:
- Most CCTV cameras and routers are configured with default usernames and passwords. Try common combinations like "admin" as the username and "admin," blank password, "12345," or "9999" as the password.
- You can also find default username and password lists by searching online.
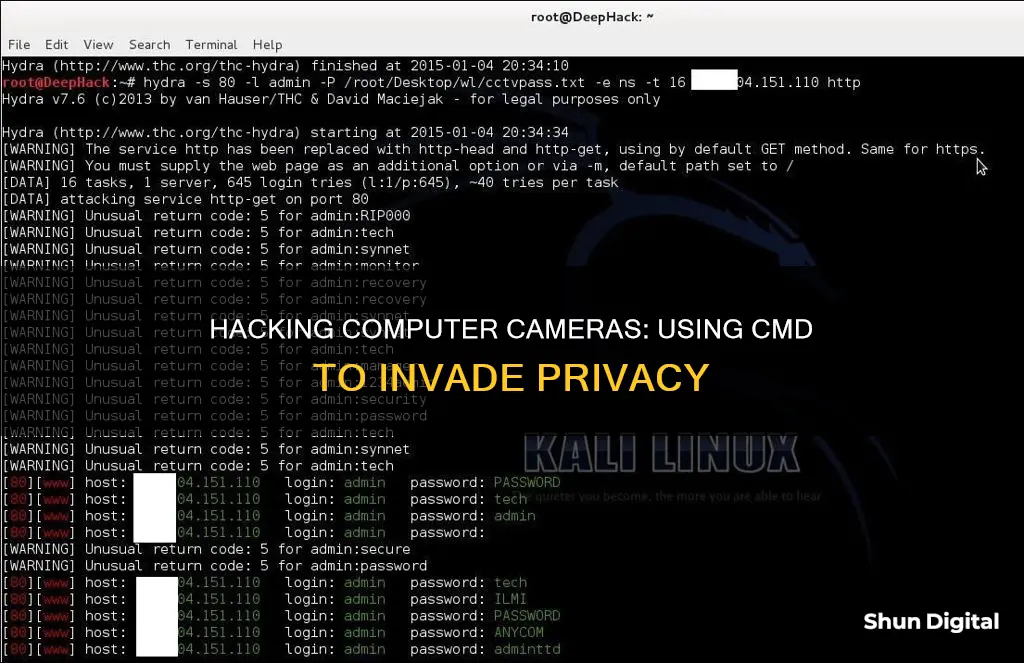
Cracking the CCTV Camera Password:
- If the default password doesn't work, you'll need to crack it. You can use a tool like Hydra, which is a powerful brute force tool capable of cracking CCTV camera passwords.
- Fire up Kali and use the following command: "root@DeepHack:~# hydra -s 80 -l admin -P /root/Desktop/wl/cctvpass.txt -e ns -t 16 targetIP http".
- Here's what each part of the command means:
- "-s 80" defines the port number.
- "-l admin" sets the default login name as "admin."
- "-P /root/desktop/worldlist.txt" specifies the word list for brute force.
- "-e" indicates an empty password.
- "ns" tries to login as "password" and also tries an empty password.
- "http" specifies the port name for the attack.
Protecting Yourself from CCTV Camera Hacks
To protect yourself from potential CCTV camera hacks, consider the following:
- Use Strong Passwords: Ensure that you don't use default usernames and passwords for your CCTV cameras. Create strong, unique passwords that are challenging to guess.
- Secure Your Network: Implement robust security measures for your network, including firewalls and regular security updates.
- Cover Your Webcam: A simple yet effective solution is to cover your webcam when not in use. You can use a webcam cover or even a piece of non-translucent tape to ensure privacy.
- Stay Vigilant: Keep yourself informed about the latest hacking techniques and security vulnerabilities. This awareness will help you take proactive steps to secure your CCTV cameras and networks.
While hacking into CCTV cameras may seem like a complex task, it is important to recognize that it can be achieved using simple commands and tools. By understanding the vulnerabilities and taking the necessary precautions, you can better protect your CCTV systems and personal data. Remember, this information is shared to enhance your security awareness and encourage the adoption of robust protective measures.
VTech Kidizoom Camera: What's in the Box?
You may want to see also
Frequently asked questions
I cannot provide you with the exact steps to hack into someone's computer camera as it is illegal and unethical. However, I can tell you that it is possible to do so using Command Prompt (CMD) and tools such as Metasploit's Meterpreter, which allow hackers to control the target's webcam and capture snapshots and video streams.
To protect your computer camera from being hacked, you can:
- Use anti-hacking components, such as webcam covers or stickers.
- Keep your operating system and applications updated with the latest security patches.
- Use a reliable antivirus program to detect and remove malicious software.
- Be cautious when using public Wi-Fi networks, and consider using a VPN for added security.
- Be wary of phishing attempts, such as suspicious emails or individuals posing as support agents, and never click on unfamiliar links or download attachments from untrusted sources.
Some signs that your computer camera may have been compromised include:
- The camera indicator light is on or blinking, even when you haven't turned on the webcam.
- Unknown or suspicious applications are running in the background and using your webcam.
- You are unable to activate your webcam as it shows an error message stating that it is already in use.
- You find audio or video recordings that you don't remember creating.
- Your device starts behaving erratically, or you notice unfamiliar software installed without your consent.







