Surveillance cameras are meant to prevent unwanted access, but ironically, they can be hacked, allowing unwanted access to the camera feed. This can be done by accessing the camera's IP address and default password, which many businesses do not change. Hackers can also access the network the camera is connected to and then weave their way into the camera itself. Once a surveillance camera is hacked, the hacker can monitor or take control of it. This can have serious consequences, as the hacker can then use the camera to snoop around and collect sensitive information.
| Characteristics | Values |
|---|---|
| Ease of Hacking | Varies from simple to complex |
| Hacker's Intent | For fun, financial gain, or to expose vulnerabilities |
| Surveillance Camera Type | Internet Protocol (IP) cameras |
| Surveillance Camera Manufacturer | Hikvision, Dahua |
| Vulnerability | Backdoors, outdated security software, default passwords |
| Solution | Two-factor authentication, multi-factor authentication, complex passwords, regular updates |
What You'll Learn

Gaining remote access to a business's video surveillance systems
The ability to remotely view and manage a video surveillance system is a powerful feature that allows business owners to monitor their premises from anywhere in the world. Here are some detailed instructions and tips to gain remote access to a business's video surveillance system:
Understanding the Basics
- Internet Connection: Ensure that the surveillance system is connected to a high-speed internet connection. This will enable remote access from any internet-connected device.
- Device Compatibility: Check that the surveillance system is compatible with your device (computer, smartphone, etc.). Most modern systems offer cross-platform compatibility, allowing access from various operating systems.
- Security Measures: Understand the security measures provided by the system, such as encryption, firewalls, and two-factor authentication. These measures protect against unauthorized access and data breaches.
Setting Up Remote Access
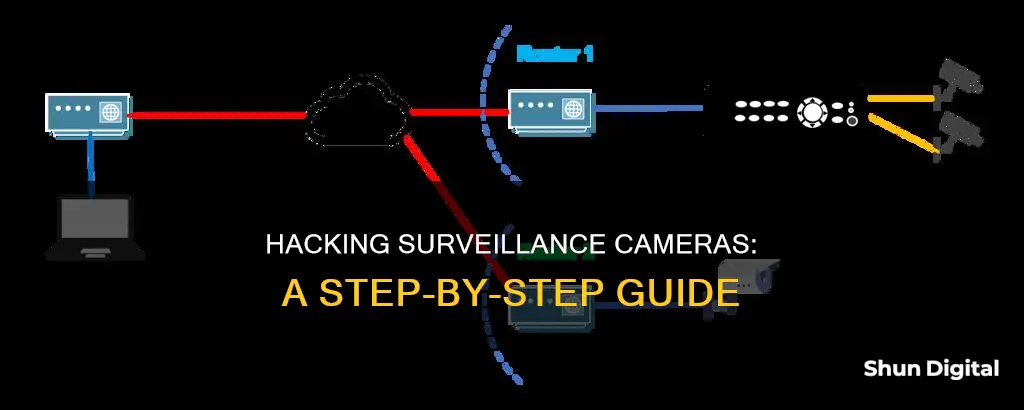
- Connect to Router: Physically connect the surveillance system to a router using an Ethernet cable. This provides an internet connection and allows remote access.
- Configure Network Settings: Set up the necessary network settings, such as IP addresses, port forwarding, and DHCP configurations. These settings ensure the system can be accessed over the internet.
- Install Software: Install any required software or applications on the devices from which you intend to access the surveillance system remotely. This may include mobile apps or computer software.
- Login Credentials: Create secure login credentials, including usernames and passwords. Avoid using default credentials provided by the manufacturer, as these can be easily guessed by potential hackers.
- Data Encryption: Enable end-to-end data encryption if offered by the surveillance system provider. This ensures that data transmitted between the cameras and your device remains secure and unintelligible to potential hackers.
- User Access Control: Restrict user access to authorized individuals only. Grant specific permissions to employees or stakeholders who require remote access, minimizing the risk of unauthorized access.
- Mobile Access: For smartphone access, download the appropriate mobile application and configure the necessary settings. This allows you to monitor the surveillance system on the go.
Best Practices and Security Tips
- Strong Passwords: Use strong and unique passwords for your accounts and Wi-Fi network. Avoid common phrases or easily guessable information. Consider using a password manager to generate and store complex passwords.
- Regular Updates: Keep your surveillance system, cameras, and associated software up to date with the latest patches and security fixes. Enable automatic updates where possible to ensure you have the latest protections.
- Data Storage: Evaluate the data storage methods used by the surveillance system. Consider using local storage options or offline storage to reduce the risk of data breaches associated with cloud storage.
- VPN Usage: Utilize a virtual private network (VPN) to add an extra layer of security to your internet connection. This is especially useful when accessing the surveillance system from public or unsecured networks.
- Monitor User Activity: Regularly review user access logs and monitor for any suspicious activity. This helps identify potential unauthorized access attempts or internal threats.
- Employee Training: Educate employees about the importance of cybersecurity and the potential risks associated with video surveillance systems. Establish clear guidelines for accessing and using the system.
- Firewalls: Enable firewalls on your devices and networks to create a barrier between your systems and potential threats. Firewalls help block unauthorized access attempts and protect against malicious activity.
- Two-Factor Authentication: Whenever available, enable two-factor authentication for an extra layer of security during the login process. This requires an additional form of verification, such as a code sent via email or SMS, in addition to a password.
Best Battery Adapters for Moultrie Cameras: Power Options Explored
You may want to see also

Using default passwords to access cameras
Default passwords are a common way for hackers to gain access to surveillance cameras. Many manufacturers set default passwords for their cameras, which can be easily found online. This makes it simple for attackers to take control of the camera, change its settings, or watch the video feed. The use of default passwords is considered poor practice, as it leaves the camera vulnerable to attack. In some cases, manufacturers have been found to bury default password information in PDF manuals or not provide it at all, making it difficult for users to find this information when needed.
To prevent unauthorised access, it is recommended that users create unique and strong passwords for their surveillance cameras, especially if the cameras are accessible over the internet. A strong password typically includes a mix of uppercase and lowercase letters, numbers, and special characters. Additionally, it is important to keep passwords secure and documented in a safe location.
It is worth noting that some manufacturers, such as Hanwha, Hikvision, and Panasonic, now require unique passwords by default and prompt users to create strong passwords during the initial setup or login. This helps to enhance the security of their products and protect users from potential attacks.
How Camera's Autofocus System Uses Red Squares to Focus
You may want to see also

Using backdoors to access camera systems
Backdoors refer to methods that allow someone to remotely access a computer system or encrypted data while bypassing the infrastructure's primary security controls. Backdoors may be intentionally installed by developers for remote tech support or smoother firmware updates, but they can also be exploited by threat actors to gain unauthorized access to a device, network, or software application.
- Hidden/Legitimate Backdoors: Software developers may intentionally install backdoors to provide remote access for legitimate functions such as customer support or troubleshooting. However, these backdoors can be exploited by hackers if they are not adequately secured. For example, in 2020, security researcher Vladislav Yarmak revealed that Chinese manufacturer Xiongmai had shipped thousands of cameras with hardware backdoors, allowing anyone to remotely access and operate the devices.
- Open Network Ports: An open port on a network accepts traffic from remote locations, creating a weak point that hackers can exploit. They target unused ports to install backdoors without triggering alerts from security software.
- Manufacturer Backdoors: Many security cameras come with a master password created by the manufacturer, which is often generic or easily guessable. Hackers can exploit these default passwords if users do not change them.
- Firmware Backdoors: Some manufacturers install backdoors in a device's firmware to provide technical support or facilitate firmware updates. However, if these backdoors are not properly secured, they can be exploited by hackers to gain easy access to the camera system.
To prevent unauthorized access through backdoors, it is essential to implement robust security measures. This includes using strong and unique passwords, regularly updating firmware and software, employing multi-factor authentication, and utilizing reputable antivirus and firewall solutions.
Battery Life of 220 Camera: How Long Does It Last?
You may want to see also

Guessing login credentials with the help of algorithms
Use Strong Passwords
Create long and complex passwords that are at least eight characters long. A combination of lowercase and uppercase letters, numbers, and special characters can make your password harder to guess. Avoid common words, personal information, and obvious choices like your name, birth date, or phone number. The longer and more complex your password is, the harder it will be for algorithms to guess correctly.
Avoid Default Passwords
Default passwords, such as "admin," "password," or "guest," are often easy to guess and pose a serious security risk. Change any default passwords as soon as possible, and make sure your new password is unique and difficult to predict.
Enable Two-Factor Authentication (2FA)
2FA adds an extra layer of security by requiring a second form of identification, such as a PIN, passcode, or biometric factor, in addition to your password. This makes it harder for algorithms to guess the correct login credentials, as they would need to crack both your password and the additional authentication factor.
Regularly Update Your Passwords
It's important to update your passwords regularly, especially if you suspect that your account may have been compromised. Changing your passwords frequently makes it harder for algorithms to guess the correct login credentials, as they would need to keep up with the changes.
Use a Password Manager
Password managers can help you generate strong, random passwords for each of your accounts, making it easier to have a variety of unique passwords without having to memorize them all. This reduces the likelihood of algorithms guessing your password correctly, as each login credential is unique and complex.
By following these guidelines, you can make it significantly more difficult for algorithms to guess your login credentials, increasing the security of your surveillance camera system and protecting your personal information.
Battery Chargers: Are They Included With Cameras?
You may want to see also

Using spoofing to trick wireless networks into registering devices
Spoofing is a tactic used in network security where a person or program successfully identifies as another by falsifying data, to gain illegitimate access. This can be used to trick wireless networks into registering devices.
Wireless security cameras are often used to secure critical locations, but they can be disabled by a hacker without disturbing the rest of the network. This is possible if the hacker is connected to the same Wi-Fi network as the security camera or if the camera is connected to a network with no password.
To spoof a wireless network into registering a device, you can use a program called Kismet to perform wireless signals intelligence in an undetectable and passive manner. This allows you to observe the wireless traffic in the area and later parse the information to find interesting devices. Kismet can identify devices by their MAC address and other details about the Wi-Fi configuration, such as default hotspot names.
Once you have identified the target device, you can use a tool like Aireplay-ng to execute a deauthentication attack, disrupting the connection between the device and the network. This involves sending authentication packets that pretend to be from the access point to the device, causing a disconnection.
It is important to note that conducting such attacks without authorization is illegal. Additionally, using Ethernet connections instead of Wi-Fi can help prevent these types of attacks as it does not allow for the same level of manipulation or sudden disconnection.
The Making of Fuji Medium Format Cameras
You may want to see also
Frequently asked questions
Hackers can gain access to surveillance cameras by exploiting vulnerabilities in the camera's software or network configuration. This can include default passwords, unpatched security software, or backdoors left open for remote access or troubleshooting.
Hackers can use access to surveillance cameras to monitor or control the camera's functions, including viewing live or recorded footage. This can be used to violate privacy, collect sensitive information, or even perform criminal activities such as identity theft or espionage.
To protect your surveillance cameras from being hacked, it is important to implement strong security measures. This includes using complex and unique passwords, enabling two-factor authentication, keeping your camera's software and firmware up to date, and ensuring your camera is purchased from a reputable source and installed by a certified professional.